The Zero Trust security model has been gaining more traction since the approach was first introduced. As cloud adoption increases every day the more we are seeing how Zero Trust is more critical than ever to start implementing.
This is because there is more of a reliance on cloud-based apps and a demand for services like SaaS, Paas, IaaS and app development platforms. They have bought many benefits like reduction in operational costs, improved scalability and increased flexibility for companies with sensitive data.
But with this increase in reliance and demand has also come an increase in the potential risk of a security breach. There are many ways to ensure resources and data are protected with the help of a Managed IT Services Company but there are also extra layers of protection that comes with a Zero Trust approach.
In this article, we will focus on implementing Zero Trust with SaaS apps to help ensure they can continue to be available and accessible for every device with a stable internet connection all while staying secure.
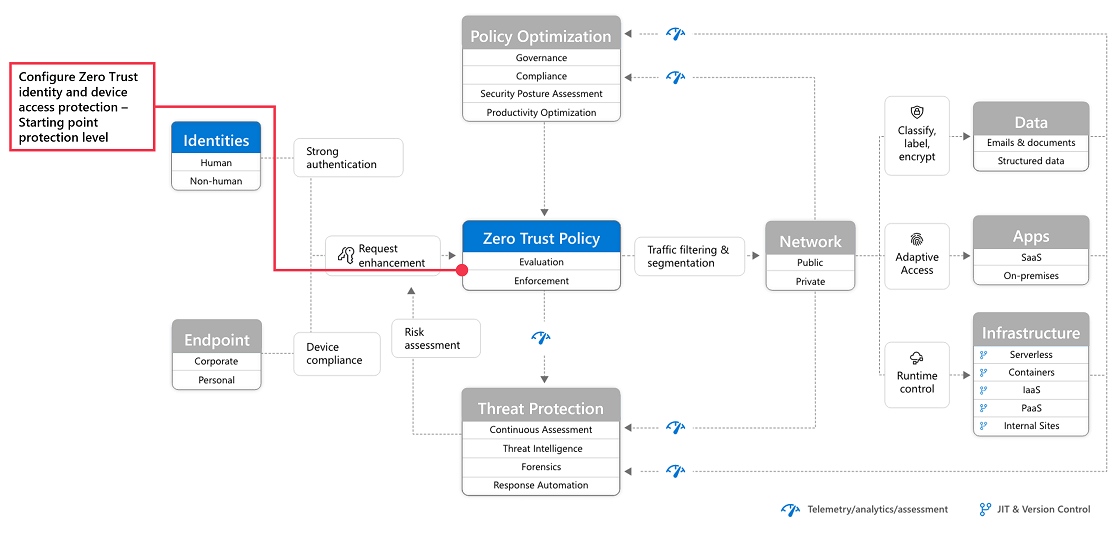
To better understand the Zero Trust model means understanding the guiding principles. These include always verifying explicitly by authenticating and authorizing, implementing least privileged access for all users and lastly, always assuming a breach with minimized blast radius, analytics and encryption verification.
With the help of TechQuarters, a trusted IT support company, we’ve broken down implementing these Zero Trust principles to your SaaS apps into three steps.
Step 1
The first step recommended is to add your SaaS apps to Azure AD and the scope of policies. Azure Active Directory is the core of Azure’s ability to manage identities and access. By adding SaaS apps users can have access to secure authentication and authorization solutions with conditional multi-factor authentication, conditional access, single-sign on, and automatic user provisioning.
You can then begin adding the apps to the scope of the company’s identity and device access policies. This allows administrators to easily define conditions for access and assign controls to actions, apps and authenticate context. This is also where multi-factor authentication can be enabled to add additional security.
Step 2
The next step according to Microsoft 365 Consulting providers is to create Defender for Cloud App policies. This is mainly to combat issues with apps that are unsanctioned that, if not managed properly, can cause significant damage. This way a company can have visibility into apps being used and properly manage and protect resources.
Defender for Cloud Apps specifically can help uncover shadow IT, assess risks, help enforce policies and investigate any suspicious activity. As a bonus, all of this can easily be done in real-time.
With Defender for Cloud Apps, it’s recommended to first discover the apps, sanction cloud-based apps, configure Conditional Access App control for those apps, enable app connectors and then apply any session controls.
Step 3
The third and final step is to deploy information protection. After you have protected access to these apps and protected session activities, you can’t forget to cover the important data that these SaaS apps can contain about the company. It’s an important step to ensure that SaaS apps are prevented from inadvertently exposing sensitive information.
To combat this users can integrate Microsoft Purview Information Protection and create policies to quickly identify which information in files is sensitive. At the core it’s all about knowing the data that needs to be protected, protecting that data and preventing any data loss from occurring.
In summary, many companies are now relying on SaaS apps. They offer ease of use, cost efficiency and flexible scalability that many can’t function without. But SaaS applications pose their own risks and Microsoft 365 has many solutions to manage all SaaS apps with controls, increased visibility and management. Cybercrime is evolving and increasing every day but implementing Zero Trust policies across all security infrastructure including the company’s SaaS apps can effectively combat any potential issues.